IoT Security for Enterprise: Challenges, Solutions, and Best Practices
Jan 24, 2025Explore the critical need for enhanced IoT security in enterprise environments. Learn about vulnerabilities, best practices, and solutions to safeguard your IoT ecosystems.
The rapid expansion of the Internet of Things (IoT) in enterprise environments presents a complex challenge: how to harness the benefits of connected devices while mitigating the inherent security risks. This article explores the critical need for enhanced IoT security for enterprise, drawing upon insights from various industry perspectives to provide a comprehensive understanding of the challenges and solutions. We'll delve into the vulnerabilities, the impact of weak security, and the best practices that organizations should adopt to safeguard their IoT ecosystems.
Understanding the Landscape of IoT Security for Enterprise
The very nature of IoT devices – their ubiquitous connectivity and often simple design – makes them attractive targets for cybercriminals. Unlike traditional IT systems, many IoT devices lack built-in security features and operate with default settings, creating potential entry points for attacks. The sheer volume and diversity of IoT devices in an enterprise network significantly expands the attack surface, demanding a new approach to security.
 Credit: www.paloaltonetworks.com
Credit: www.paloaltonetworks.com
The Challenge of Unseen Devices
One of the primary challenges in IoT security for enterprise is the "shadow IT" phenomenon, where unapproved devices connect to corporate networks. These devices, often deployed without IT oversight, can introduce significant vulnerabilities. A lack of visibility into these devices makes it difficult to assess risks and implement appropriate security measures. This also applies to devices that may be intentionally placed on the network, but have weak built-in security or use default passwords, making them easy targets.
Heterogeneity and Distribution
The diverse nature of IoT devices, both in terms of hardware and software, complicates security efforts. Manufacturers often fail to comply with universal security standards, resulting in a patchwork of vulnerabilities across the enterprise. Also, the distributed nature of IoT devices, spread across locations and potentially outside of traditional IT infrastructure, requires a security strategy that is scalable and adaptable.
Why IoT Security for Enterprise Matters
The consequences of inadequate IoT security for enterprise can be severe. Data breaches, unauthorized access to systems, and even physical damage can result from exploited vulnerabilities. The financial ramifications, coupled with reputational damage, make robust IoT security imperative.
The Growing Threat Landscape
The IoT cybersecurity market is experiencing explosive growth, reflecting the seriousness of the threat. The increasing reliance on IoT in industrial settings (IIoT), smart buildings, healthcare, and retail further amplifies the need for robust security measures. The potential economic impact of compromised IIoT systems, for example, highlights the critical importance of safeguarding these interconnected devices.
Regulatory and Compliance Pressures
Governments worldwide are enacting regulations and standards to enhance IoT security for enterprise. Regulations such as the EU Cybersecurity Act, the UK's PSTI Act, and the US Cyber Trust Mark program underscore the growing need for manufacturers and users to implement security best practices. The impact of data privacy regulations like GDPR and CCPA further complicates the landscape, as they require careful handling of personal data collected by IoT devices.
Three Pillars of Effective IoT Security for Enterprise
To effectively secure IoT environments, enterprises must implement a comprehensive strategy encompassing three core areas: Visibility, Segmentation, and Protection. These pillars must be applied to all levels of the technology stack, from the device hardware to network communications and service interfaces.
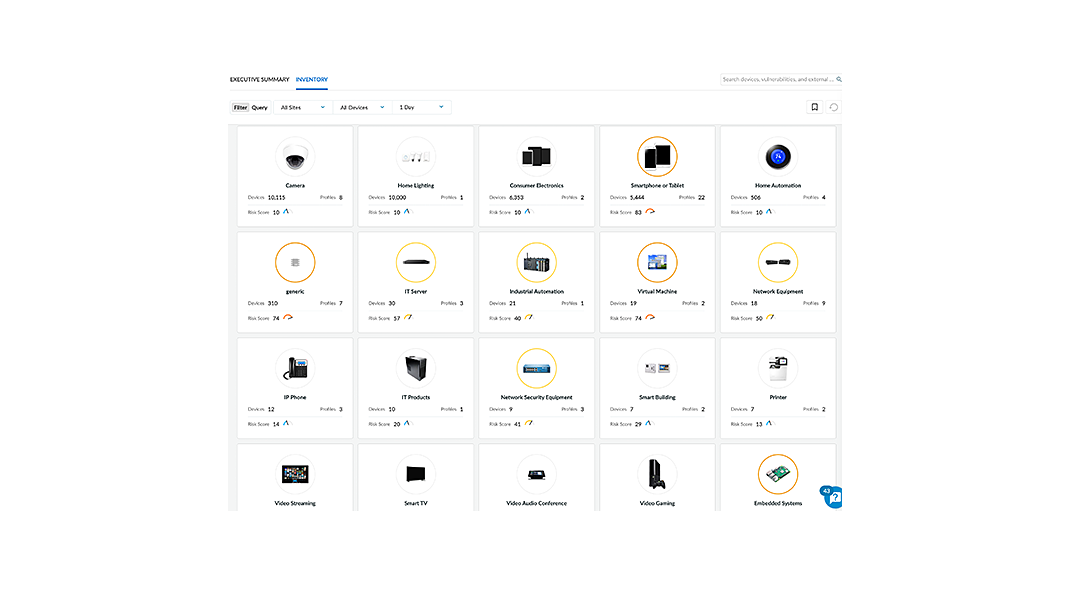
1. Visibility: Discover and Assess Every Device
![]() Credit: www.checkpoint.com
Credit: www.checkpoint.com
Gaining complete visibility across all connected devices is the first crucial step. This involves:
- Automated Device Discovery: Utilizing solutions that can automatically identify and classify all devices, both managed and unmanaged, within the network. This includes discovering devices that may be operating on the network without explicit authorization.
- Comprehensive Device Profiling: Understanding each device's type, vendor, model, and unique attributes. This allows for a more targeted and effective approach to security.
- Real-Time Risk Assessment: Continuously monitoring device behavior for anomalies, vulnerabilities, and potential threats. This includes identifying devices with known CVEs, outdated software, or unusual network activity.
2. Segmentation: Enforce Least Privilege Access
 Credit: www.fortinet.com
Credit: www.fortinet.com
Network segmentation is crucial for limiting the impact of a potential breach. Key strategies include:
- Granular Policies: Creating context-rich policies that isolate IoT devices from the rest of the network and from each other.
- Least Privilege Access: Implementing strict access controls, ensuring each device only has the necessary permissions to perform its designated functions.
- Dynamic Segmentation: Employing solutions that can automatically adapt security policies based on the risk profile of a device, isolating devices exhibiting suspicious behavior.
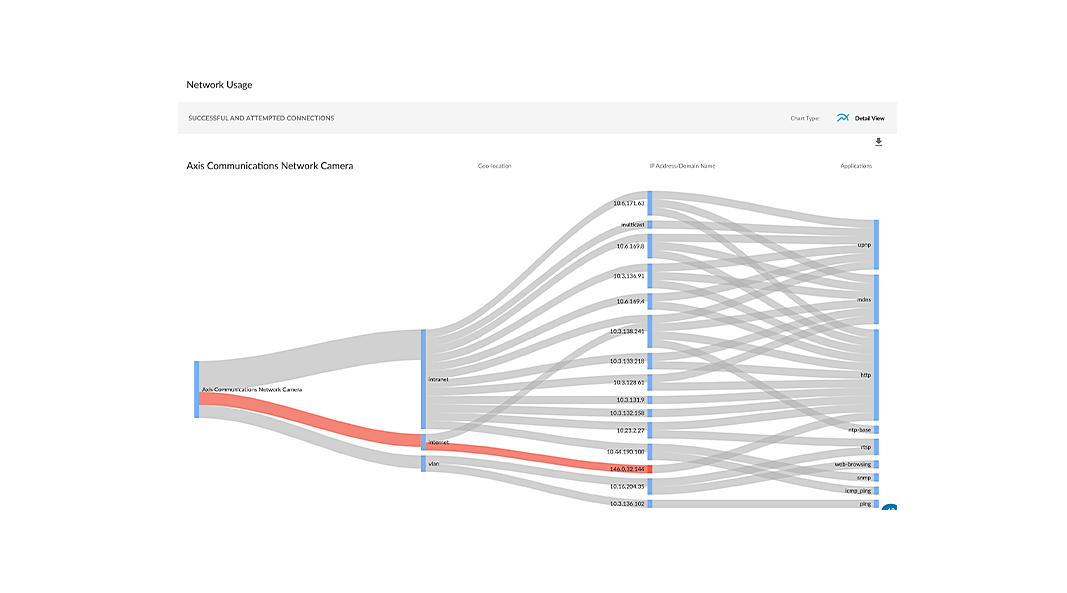
3. Protection: Prevent Known and Unknown Threats
 Credit: www.paloaltonetworks.com
Credit: www.paloaltonetworks.com
Protecting IoT devices requires a multi-layered approach:
- Threat Intelligence: Utilizing real-time threat intelligence feeds tailored to IoT devices to block known exploits, malware, and command-and-control (C2) communications.
- Anomaly Detection: Employing machine learning to identify unusual device behavior, indicating a potential zero-day attack or compromise.
- Automated Response: Implementing automated workflows that can quickly isolate devices exhibiting malicious behavior to prevent lateral movement and further damage.
- Firmware Updates: Ensuring that devices receive regular firmware updates and security patches to address newly discovered vulnerabilities, whether manually or via over-the-air (OTA) updates.
- Data Encryption: Implementing strong encryption schemes to protect data both in transit and at rest. This includes Transport Layer Security (TLS), Advanced Encryption Standard (AES), and other relevant encryption algorithms.
Implementing Strong Authentication and Authorization
A critical aspect of IoT security for enterprise is robust authentication and authorization mechanisms. Weak passwords and default credentials are common vulnerabilities that attackers exploit. Best practices include:
- Digital Certificates: Leveraging public key infrastructure (PKI) and digital certificates for device authentication and secure communication.
- Multi-Factor Authentication (MFA): Enforcing MFA where possible to make it more difficult for attackers to exploit compromised credentials.
- Secure Default Settings: Ensuring devices are designed to minimize the risk of weak default passwords, by eliminating hardcoded credentials, forcing password changes upon setup, and enforcing strong, random passwords.
Addressing Specific IoT Security Challenges
Beyond the core pillars, there are several specific challenges that enterprises must address when securing IoT:
- Insecure Communication Protocols: IoT devices often use insecure protocols like HTTP and Telnet, which are vulnerable to eavesdropping and attacks. Employing secure protocols, such as HTTPS and SSH, is essential.
- Lack of Encryption: Many IoT devices transmit unencrypted data, making them susceptible to man-in-the-middle attacks. Encryption should be implemented to protect data both in transit and at rest.
- Vulnerabilities in Firmware and Software: The short development cycles and low price points of many IoT devices often result in firmware and software vulnerabilities that can be exploited by cybercriminals. Regular patching and updates, along with firmware integrity checks, are crucial.
- Patching and Updating Devices: Many IoT devices aren't designed to receive regular security updates, making them vulnerable to attacks. Solutions are needed to ensure secure upgrades, firmware updates, and dynamic testing.
Leveraging IoT Detection Services
To effectively manage IoT security for enterprise, organizations should consider implementing IoT detection services. These services provide visibility into all connected devices, monitor for anomalies, and enforce security policies. Key capabilities include:
- Continuous Monitoring: Analyzing device activity patterns to detect deviations from normal behavior.
- Real-Time Alerts: Providing immediate notifications of potential threats and security breaches.
- Virtual Patching: Offering the ability to apply patches and security updates without the need for manual intervention on individual devices.
The Path Forward for IoT Security in Enterprise
Securing IoT in the enterprise is not a one-time task but an ongoing process that requires continuous monitoring, adaptation, and improvement. By understanding the unique challenges, adopting robust security measures, and staying abreast of evolving threats and technologies, organizations can leverage the power of IoT without compromising their security. The key is to prioritize IoT security for enterprise as a core component of any cybersecurity strategy.
 Credit: www.techtarget.com
Credit: www.techtarget.com
The path to secure IoT involves:
- Implementing Zero Trust: Adopting a Zero Trust approach where no device or user is implicitly trusted, requiring continuous verification and authorization.
- Integrating Security into the Development Cycle: For IoT manufacturers, building security into devices from the design phase is crucial, ensuring secure hardware, firmware, and software.
- Prioritizing User Education: Educating users about the risks associated with IoT devices and promoting secure usage practices.
- Continuous Improvement: Regularly reviewing and updating security policies and solutions to adapt to the ever-evolving threat landscape.
By embracing these strategies, enterprises can confidently leverage the benefits of IoT while ensuring the security and integrity of their data, systems, and operations.
Common Smart Home Mistakes and How to Fix Them
Published Feb 19, 2025
Avoid common smart home pitfalls by understanding and fixing these mistakes. Learn how to optimize your smart home for convenience, security, and efficiency....
Ensuring Smart Plug Safety for Winter Devices: A Comprehensive Guide
Published Feb 18, 2025
Ensure smart plug safety for winter devices with our comprehensive guide. Learn how to prevent accidents, save energy, and enjoy a secure home throughout the season....
Supercharge Your Smart Home: 5 Must-Try Google Gemini Tips and Tricks
Published Feb 18, 2025
Unlock the full potential of your smart home with Google Gemini! Discover 5 must-try tips and tricks for effortless control, natural language commands, and AI-powered automation....